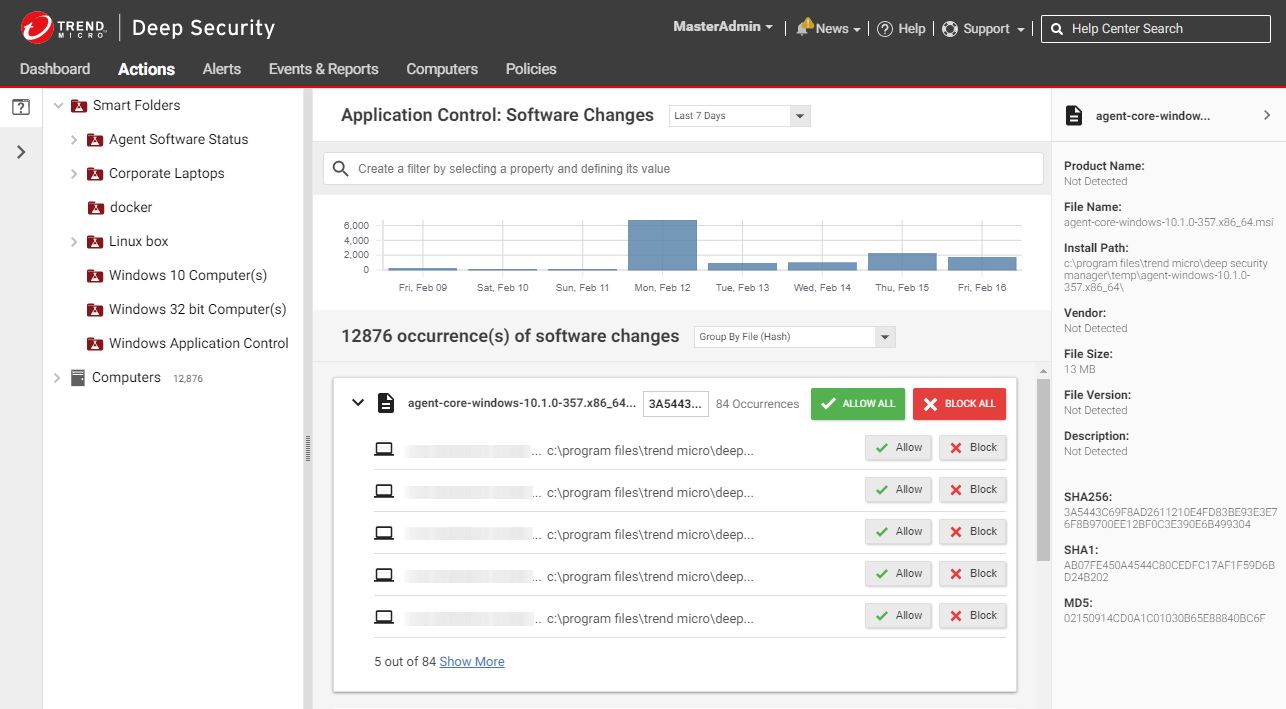
Blocking Applications in Trend Micro Worry-Free Business Security Antivirus - Managed Services IT Provider | Outsourced IT Services Mirazon

Endpoint Application Control | TrendMicro | MSP Navigator. Discover products, services and experts that can help you achieve your goals.
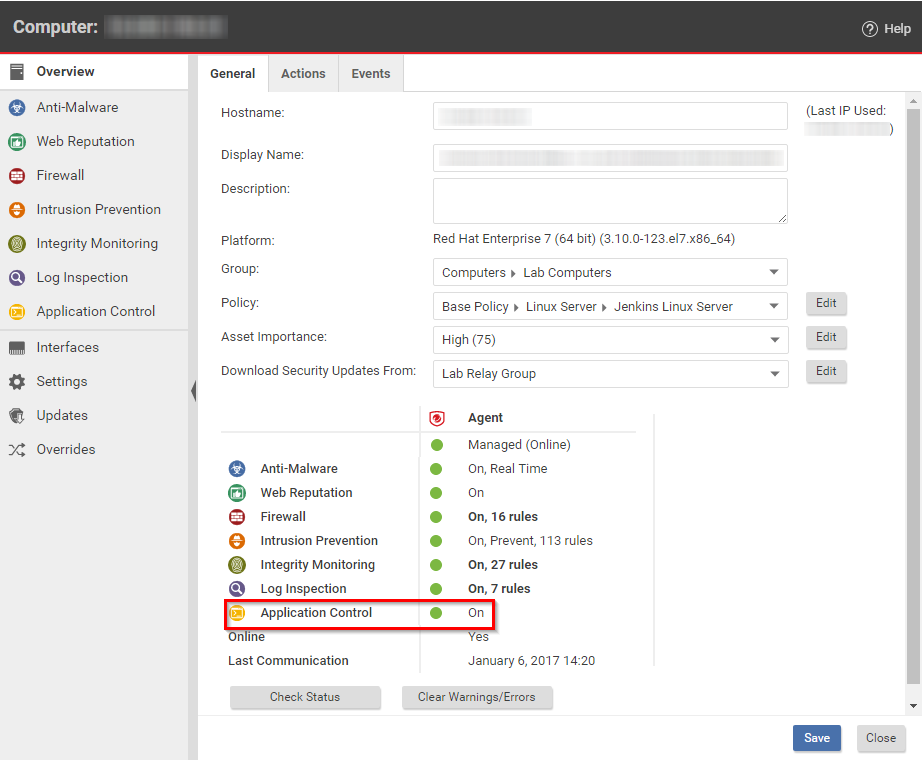
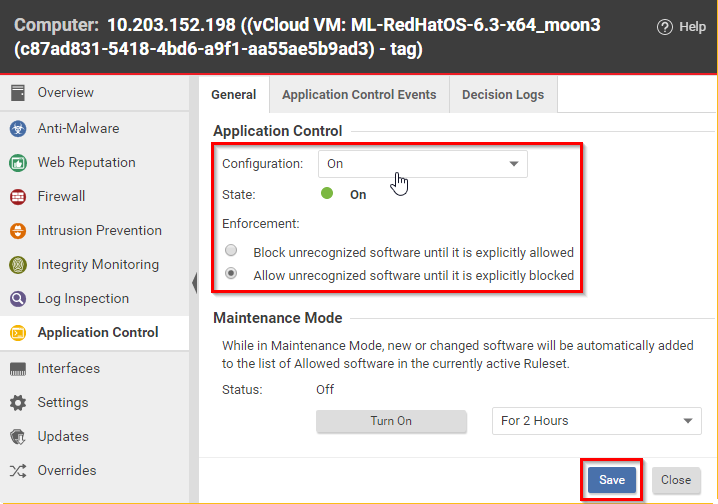
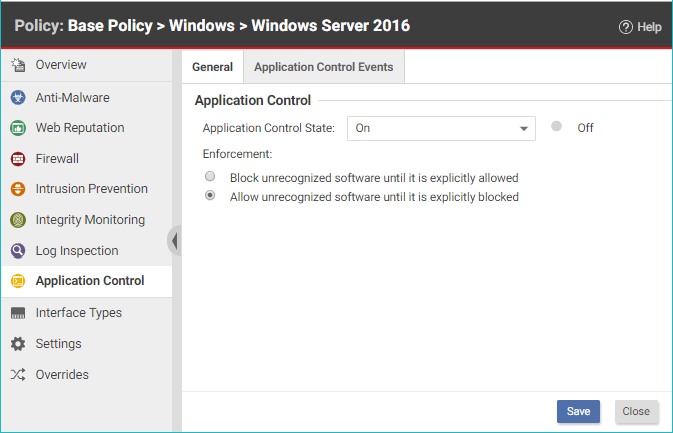
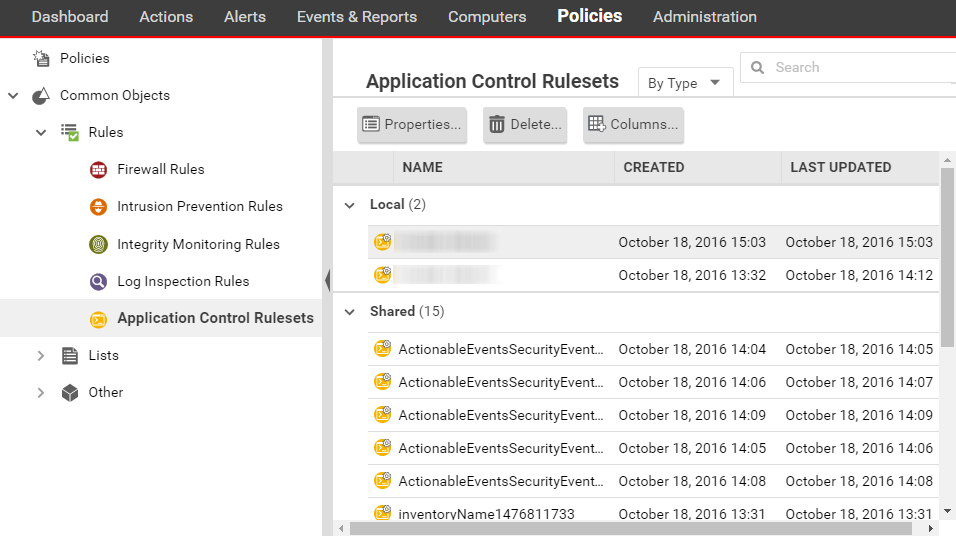
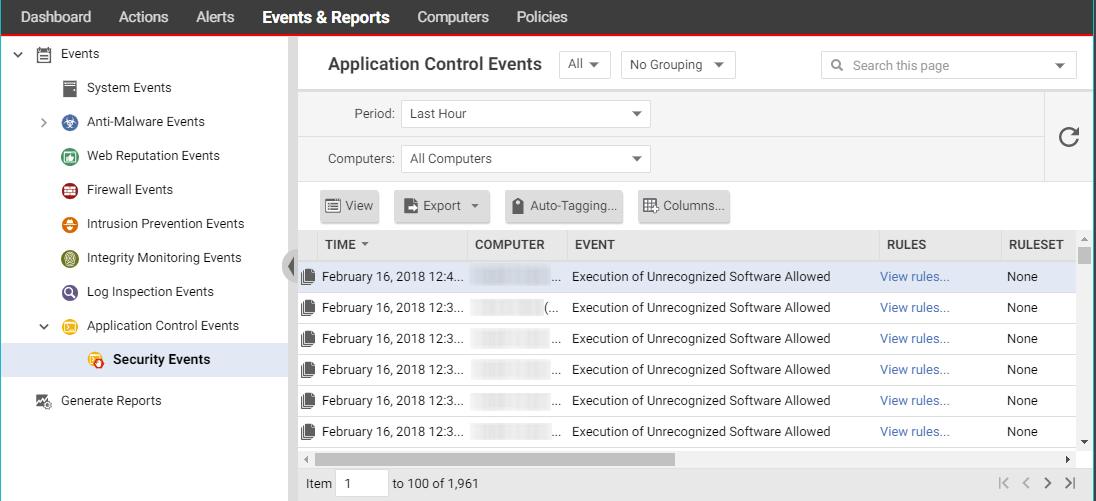
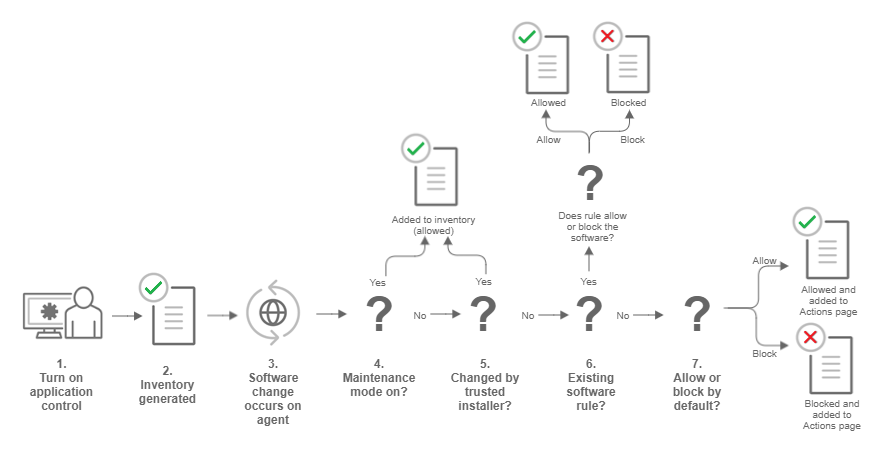
Verify that Application Control is enabled - Workload Security | Trend Micro Cloud One™ Documentation